

How a CASB Integrates with an On-Premises DLP Solution
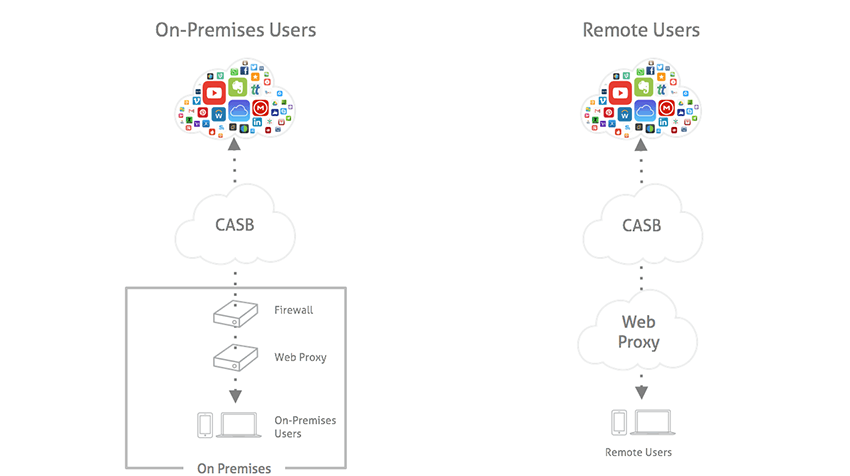
How a CASB Integrates with an On-Premises DLP Solution Deployment architecture for enforcing DLP policies with a CASB and registering enforcement actions in an on-premises DLP solution. If you use an on-premises data loss prevention solution such as Symantec DLP, RSA...








