Watch How Balbix’s Risk-Based Vulnerability Management Platform Works
Why Choose Balbix?
Security teams are pulled in many directions– vulnerability management, incidence response, deployment and tuning of security tools, application security, dashboarding and reporting, etc.
- Do you know if you are working on the right projects?
- Where are the riskiest areas of your attack surface?
- Can you quantify the progress you are making?
Balbix enables you to address these challenges and make the right decisions in order to transform your cybersecurity posture and reduce breach risk.
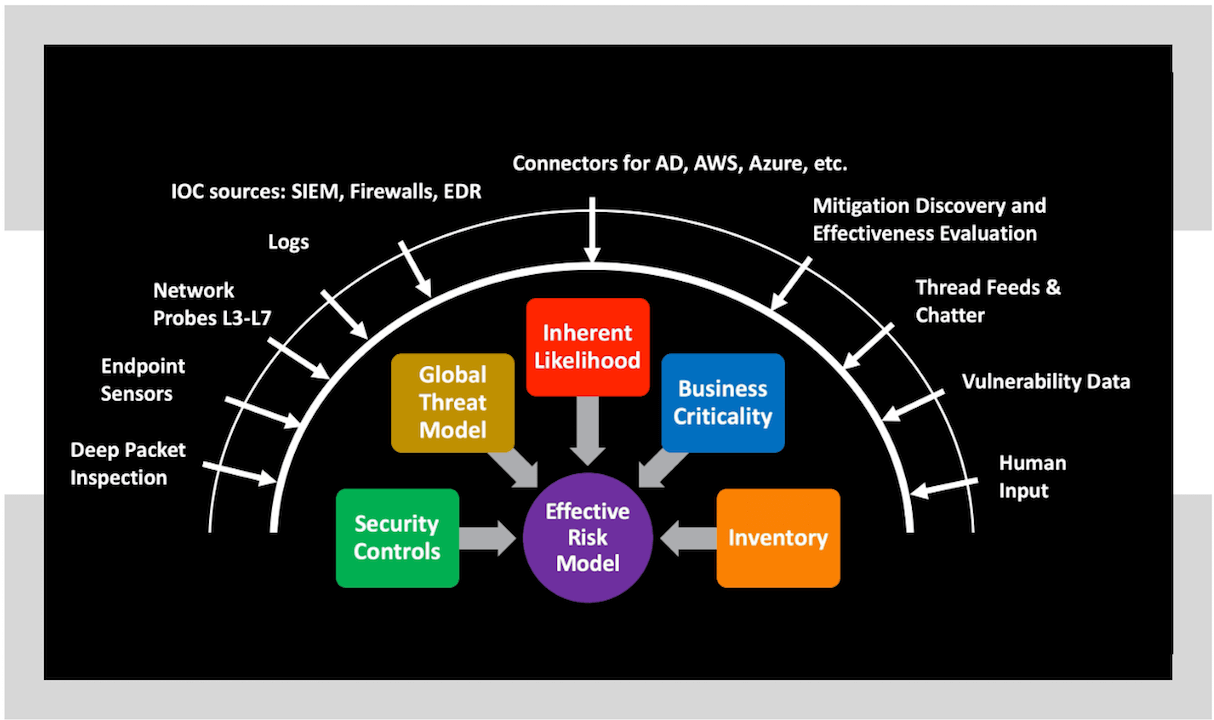
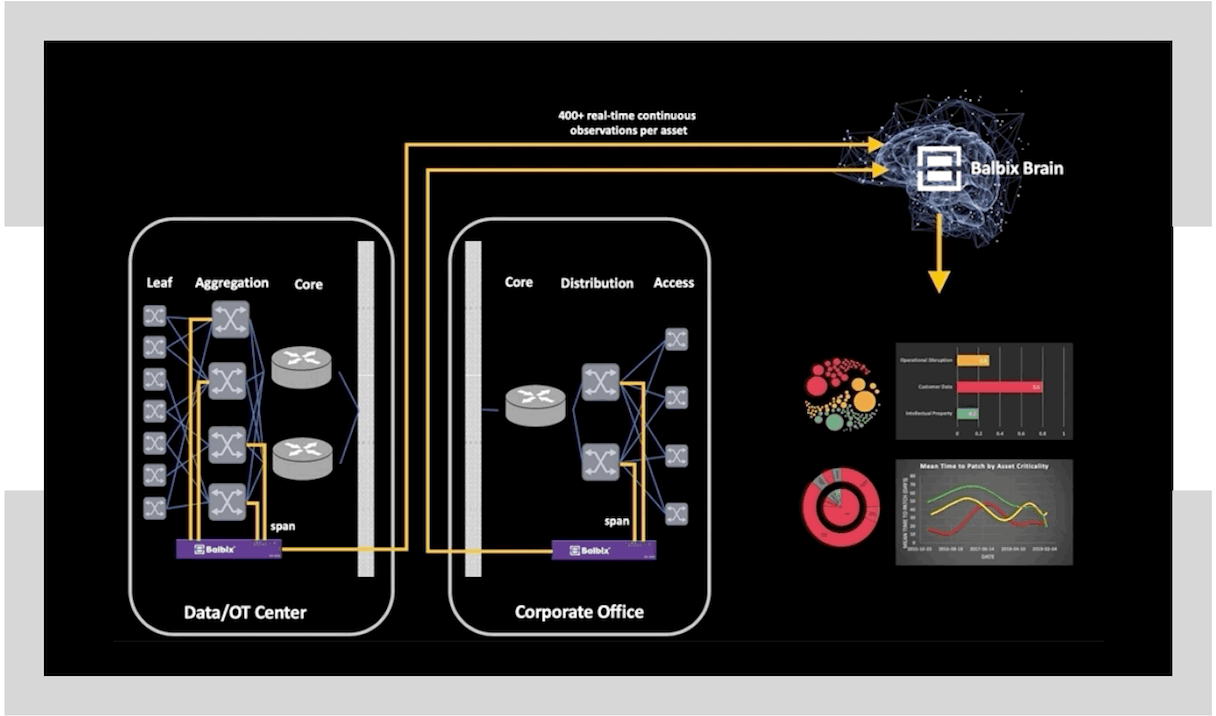
To accurately quantify breach risk, Balbix continuously analyzes up to several hundred billion time-varying signals from your network.
You can understand your real-time risk with Balbix’s drill-down risk heatmaps and natural-language search.
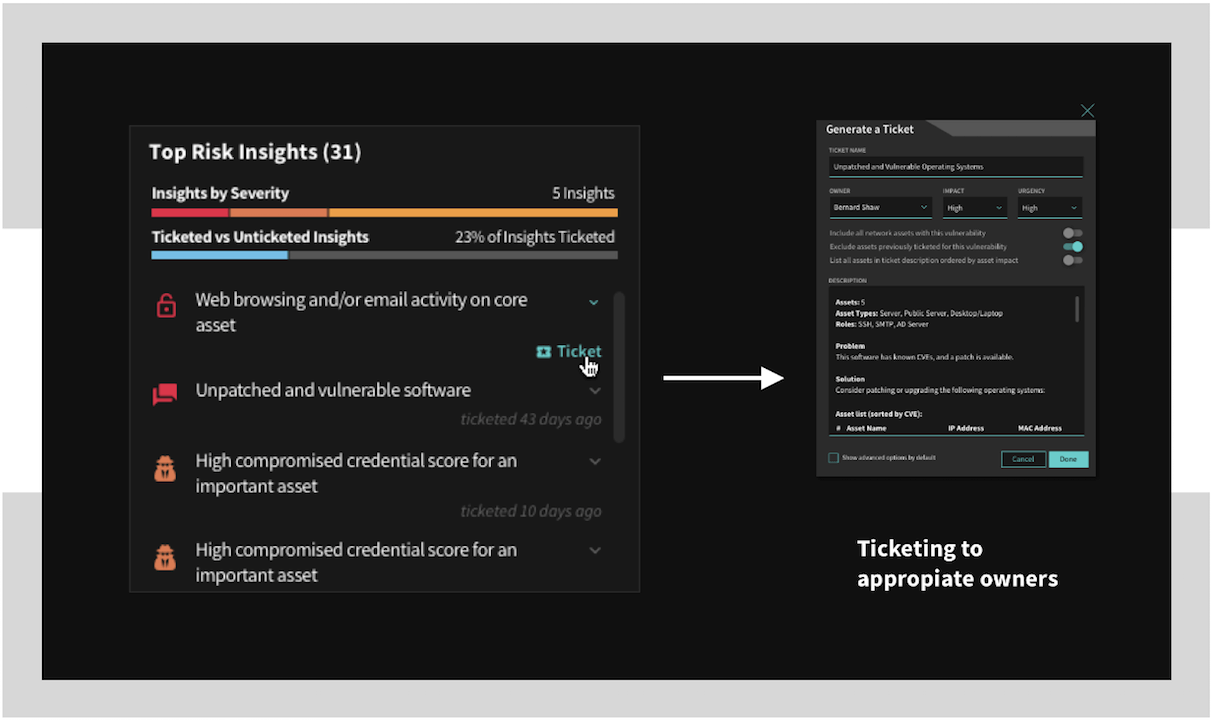
Balbix generates prioritized tickets with relevant context assigned to the right owners for strategic and tactical mitigating actions. Notifications, leaderboards and incentives can be set up for a gamified approach to drive cyber-risk reduction.
- Sensors, connectors, and collectors deployed across your network continuously discover and monitor your devices, apps, and users across 100+ attack vectors.
- The Balbix Brain uses specialized AI to predict likely breach scenarios and prescribes a prioritized set of necessary actions to improve cybersecurity posture.
- Integrations with ticketing and orchestration systems enable you to operationalize the transformation and maintenance of your cybersecurity posture.
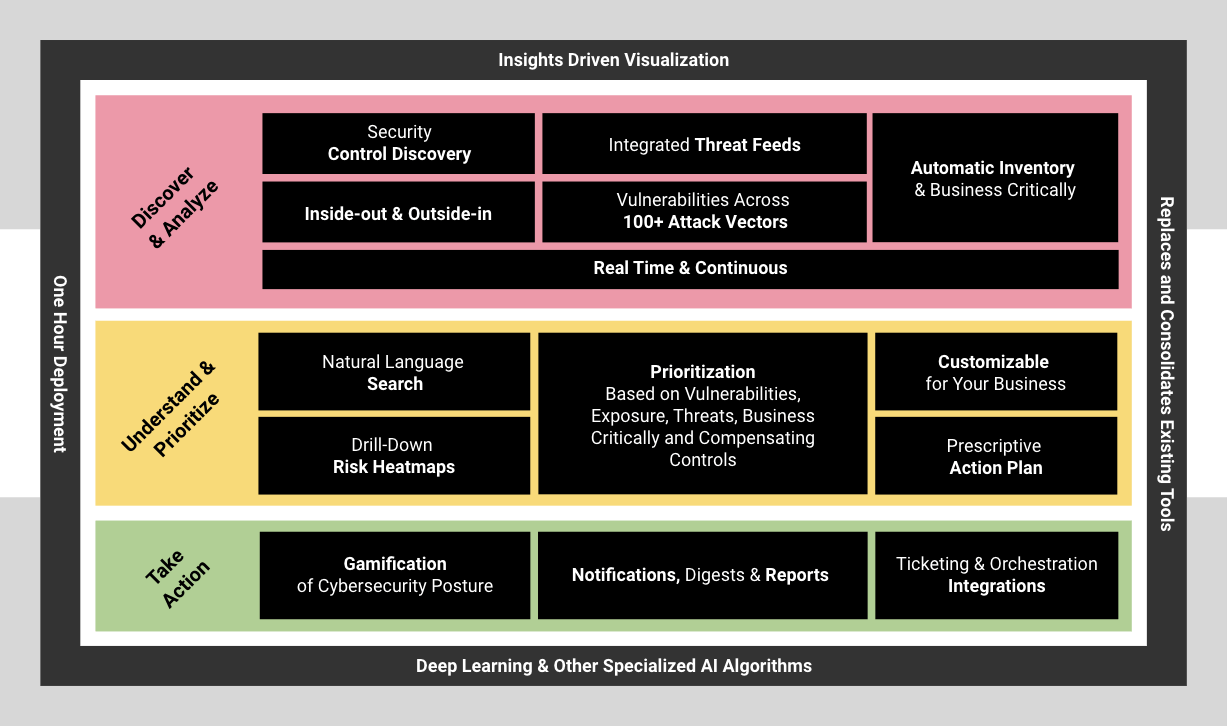
AI-Powered Cybersecurity Posture Transformation
Balbix’s Unique Capabilities
Converged Platform
Converged Platform
Balbix is a converged platform to harness the power of AI and gamification for cybersecurity posture transformation.
- Real-time view of your cybersecurity posture with insights on how to reduce breach risk.
- Balbix replaces many point products that cover different parts of your attack surface with a single system. You minimize multi-vendor complexity and reduce tool fatigue.
You can explore each Balbix feature in detail to see how it may help you improve the effectiveness of your cybersecurity program and drive rapid cybersecurity posture transformation.
Real-Time & Continuous
Real-Time & Continuous
The Balbix platform offers real-time and continuous monitoring and analysis of the entire enterprise attack surface.
- Automatic discovery and inventory of assets in real-time.
- Continuous monitoring of all assets for risk across 100+ attack vectors.
- You do not need to schedule any vulnerability scans, or perform validation scans.
- Balbix automatically incorporates information about vulnerabilities, threats, degree of exposure and your mitigations to highlight security posture issues that need to be fixed.
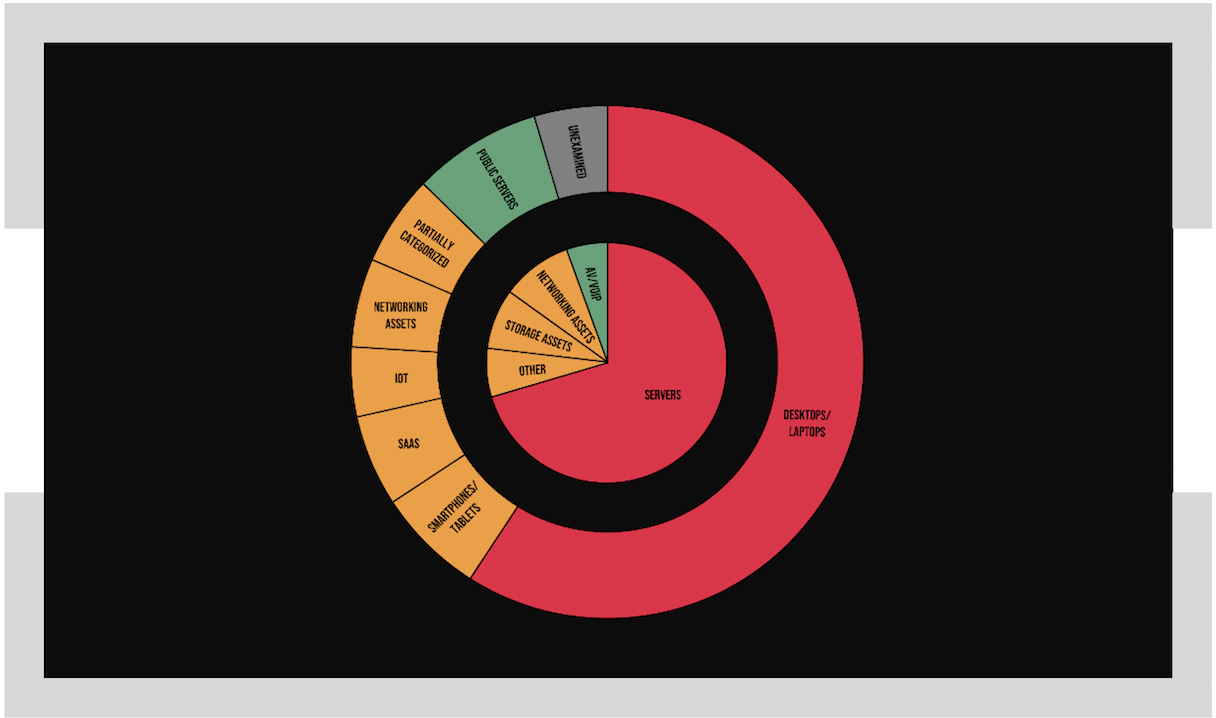
Automatic Inventory
Automatic Inventory
Balbix automatically discovers, analyzes and categorizes your inventory. This includes all devices, apps and services managed and unmanaged, infrastructure, on-prem and cloud, fixed and mobile, IoTs, ICS, etc. The inventory is available via real-time dashboards and search.
Balbix’s inventory capabilities include:
-
- Categorization of assets into core or perimeter assets.
- The relationship between assets and users (including administrators).
- Details for each asset, e.g. software and hardware version, open ports, and usage.
- Estimated breach impact for each asset.
Controls Discovery
Controls Discovery
The Balbix platform offers real-time and continuous monitoring and analysis of the entire enterprise attack surface.
- Automatic discovery and inventory of assets in real-time.
- Continuous monitoring of all assets for risk across 100+ attack vectors.
- You do not need to schedule any vulnerability scans, or perform validation scans.
- Balbix automatically incorporates information about vulnerabilities, threats, degree of exposure and your mitigations to highlight security posture issues that need to be fixed.
Prioritization
Prioritization
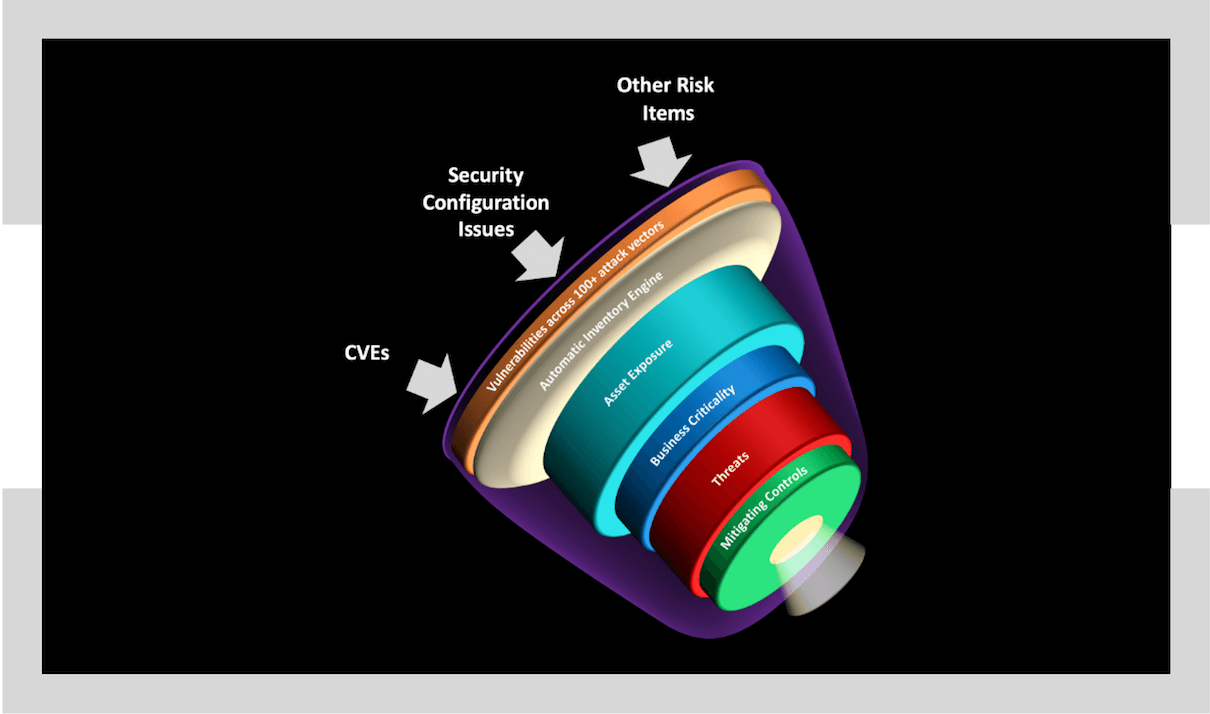
Balbix’s risk-based prioritization of security posture issues factors in 4 things:
- Vulnerability severity.
- Threat level– are attackers exploiting this vulnerability in the wild.
- Exposure, based on usage or configuration.
- The business impact if this asset is compromised.
With this framework, you can filter out issues that need immediate attention, vs those which can wait a few days, and those which are just noise.
Customizable
Customizable
Balbix lets you to define risk areas appropriate for your business using natural language search, and then maps the automatic calculation and tracking of these metrics to your actual on-network cybersecurity posture.
-
You can type “risk to intellectual property” in the Balbix search box, and define this as a risk item for Balbix to track and report on.
-
Balbix automatically maps the risk item “intellectual property” to the actual on-network assets and their attributes and that drive this risk.
-
The system continuously observes, analyzes and reports on the relevant parts of your cybersecurity posture.
Prioritization
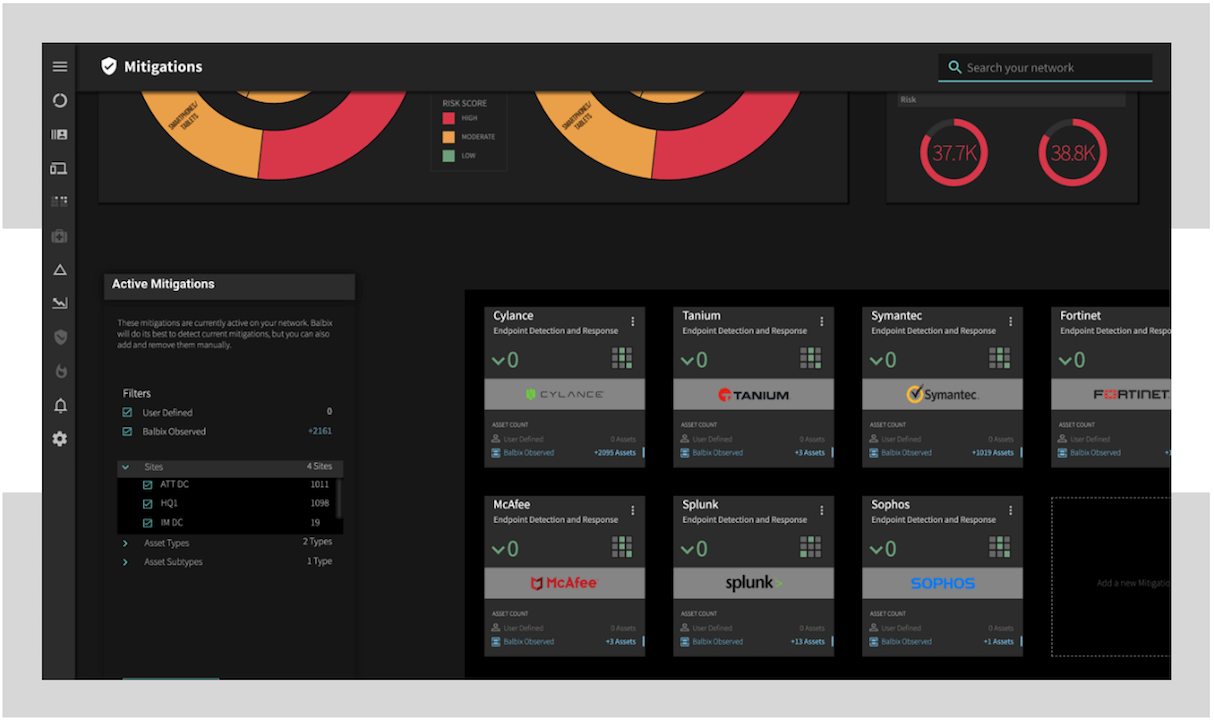
Integrations
Balbix integrates into your enterprise tools, such as ticketing and security orchestration systems.
-
You can set up business risk areas that you care about and Balbix can then automatically map vulnerabilities in these areas to the appropriate owners.
-
Based on desired SLAs for different priority levels, tickets can be automatically created, assigned to the relevant owners, and tracked.
-
As your team takes mitigating actions, Balbix automatically discovers and validates each fix.
-
APIs are available for 3rd party tools to query Balbix for context about assets and risk.
Inside-Out & Outside-In
Inside-Out & Outside-In
Unlike other products, Balbix continuously observes the extended enterprise network both inside-out and outside-in to discover your attack surface. Real-time data from multiple internal and external sources is ingested and then analyzed to produce a complete picture of cyber-risk. Data sources include:
- Balbix host, traffic and network sensors.
- Enterprise log sources (e.g DHCP, CMDB, AD, and enterprise data lakes).
- Cloud connectors and collectors for provider APIs and logs.
- Third party threat feeds.
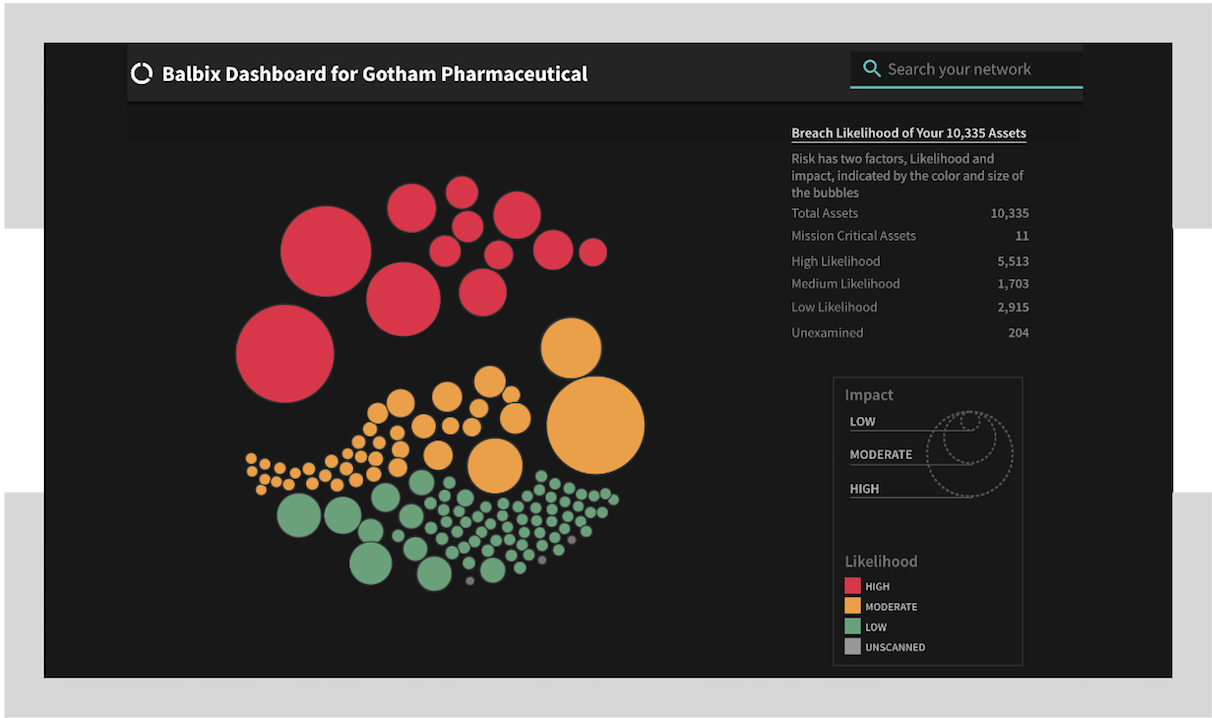
Risk Heatmaps
Risk Heatmaps
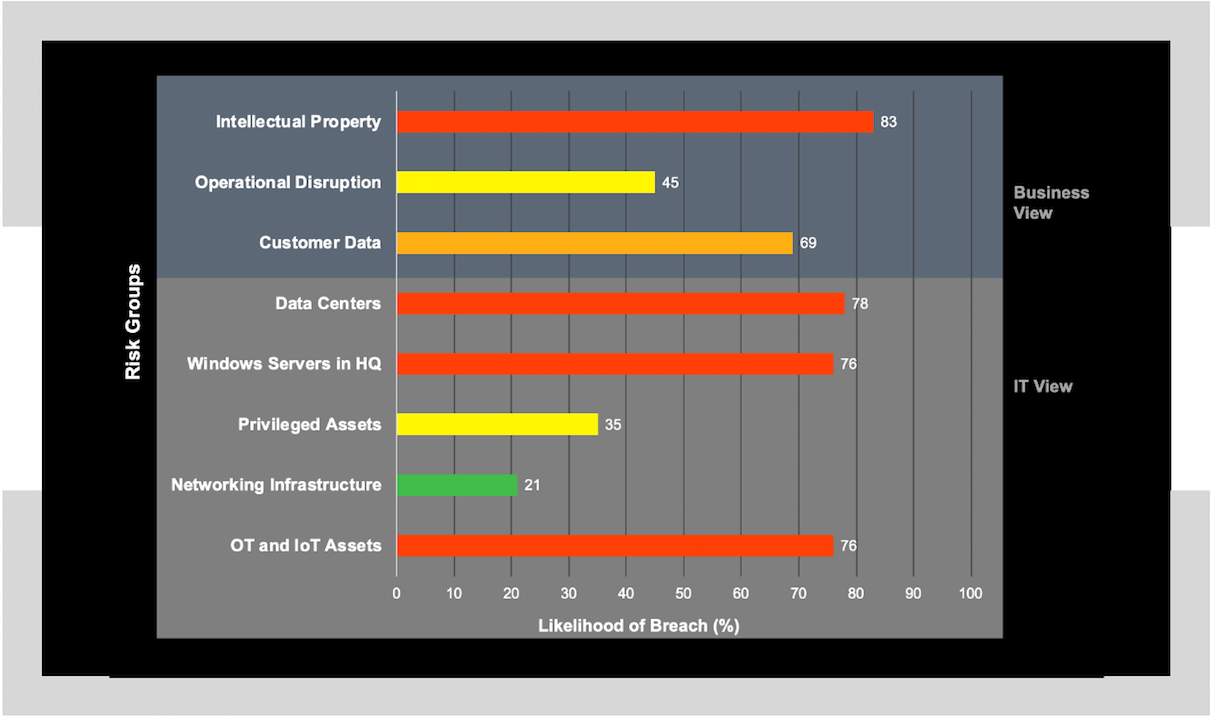
Balbix’s real-time risk heat maps show you how risk is distributed in the enterprise.
- Hover over the bubbles to get an idea of the risk distribution.
- You can drill into a bubble to see why it is red, or of a certain size.
- Gain and understanding of how the biggest risk areas can be mitigated.
- Compare how different stakeholders are managing cyber-risk.
As you fix vulnerabilities and other security posture issues, you will see this bubbles break up into smaller ones, or change color. What bubbles would you like to pop today?
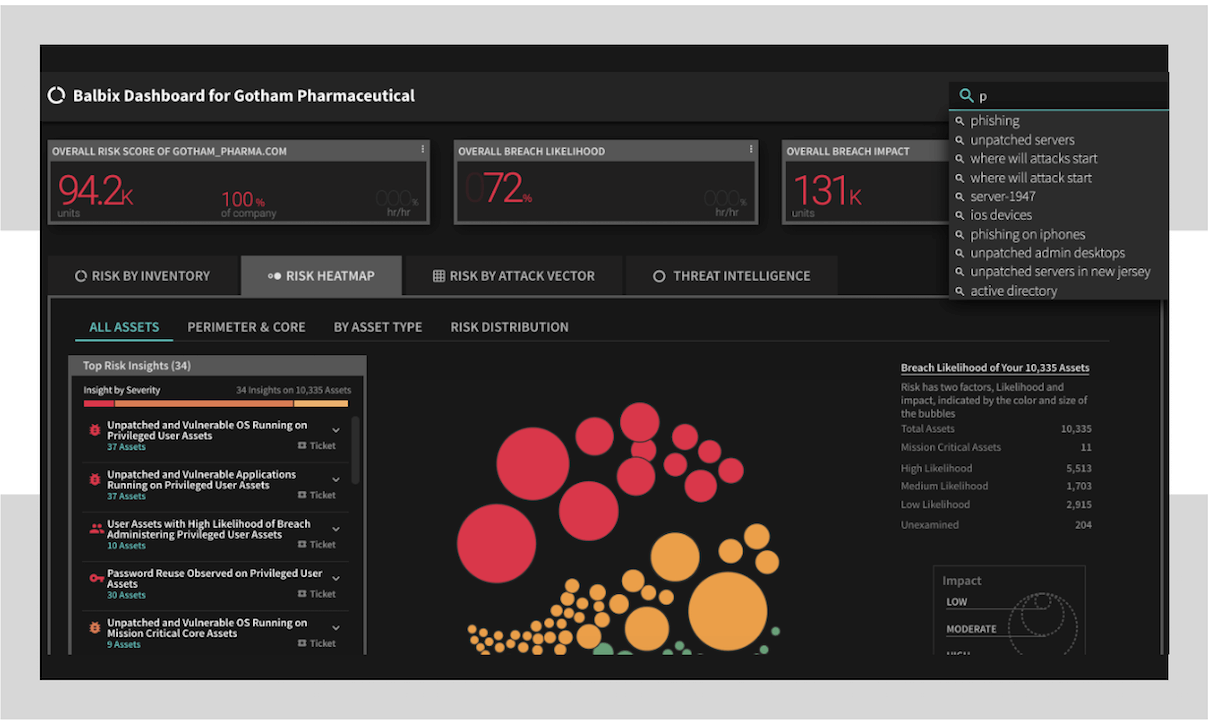
Google "like" Search
Google “like” Search
With Balbix, you can get answers to questions about your inventory, security posture or breach risk using natural language search.
- Query your inventory using IT vocabulary, e.g., “windows servers in london”, “security cameras”.
- Queries can combine security and IT terms: “unpatched switches in nyc”, “password reuse”, “phishing”.
- Search by CVE number, e.g., “CVE-2017-0144”, or its common name “wannacry”.
- Also use higher level queries like “where will attacks start”, “what will they go after”, “assets with intellectual property”, and “risk to customer data”.
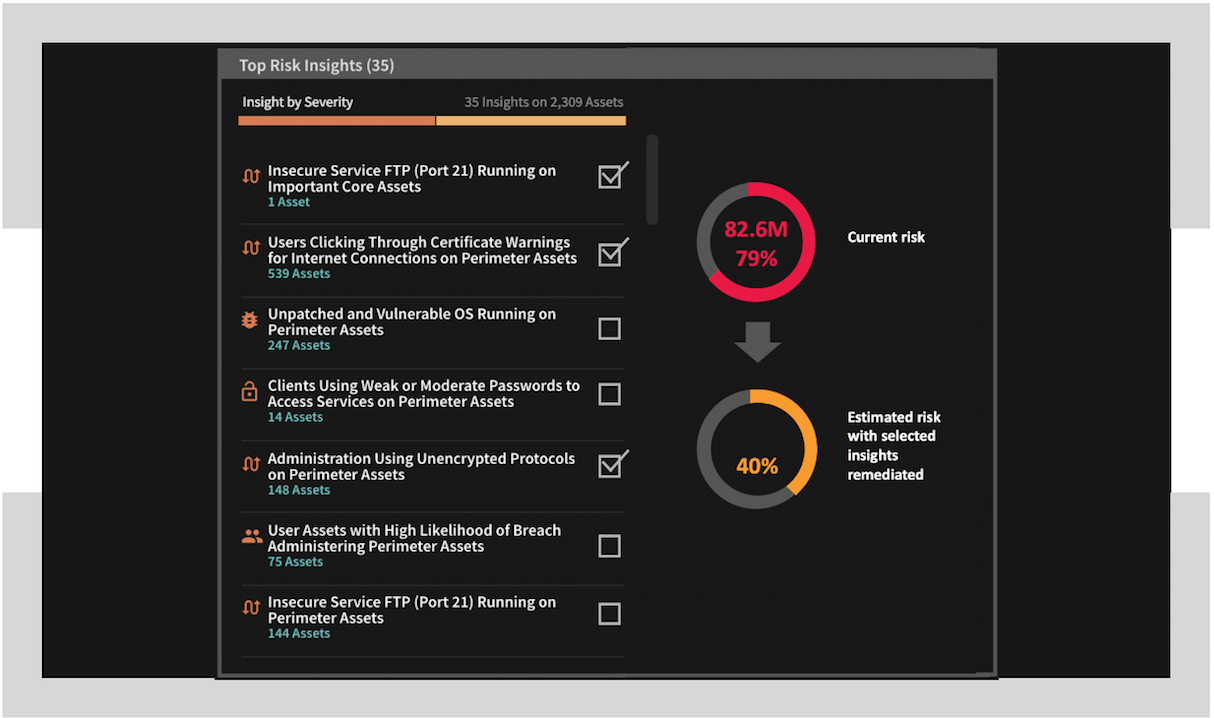
Prescriptive Plan
Prescriptive Action Plan
Balbix provides actionable insights with specific steps that you can take to improve cyber-resilience and overall cybersecurity posture.
-
All suggested risk remediation actions are prioritized based on risk.
-
Balbix provides context and tools to help you select the order in which you schedule mitigating tasks to get maximal reduction of risk.
-
When appropriate, the system provides some options for each risk insight to help you quickly implement a practical fix.
-
The prescribed mitigating actions can be ticketed to remediation owners automatically or manually.
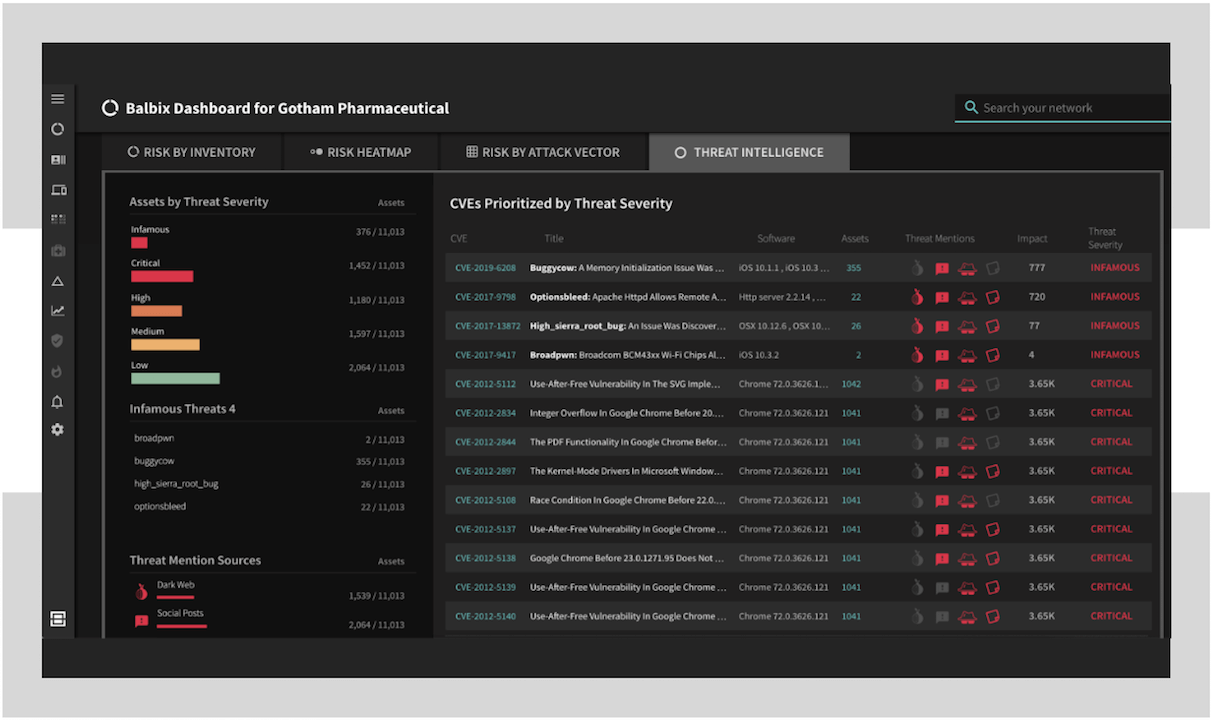
Integrated Threat Feeds
Integrated Threat Feeds
Balbix incorporates threat intelligence from our partners and public sources. This includes information from the dark web, security research forums, government advisories, exploitDB, pastebin, etc.
- Integrated threat data enables Balbix to prioritize your vulnerabilities based on what is currently fashionable with the adversary vs theoretical CVEs.
- You get to know which of your assets are susceptible to infamous threats like wannacry, sambacry, poodle, broadpwn, etc., and can take mitigating actions quickly.
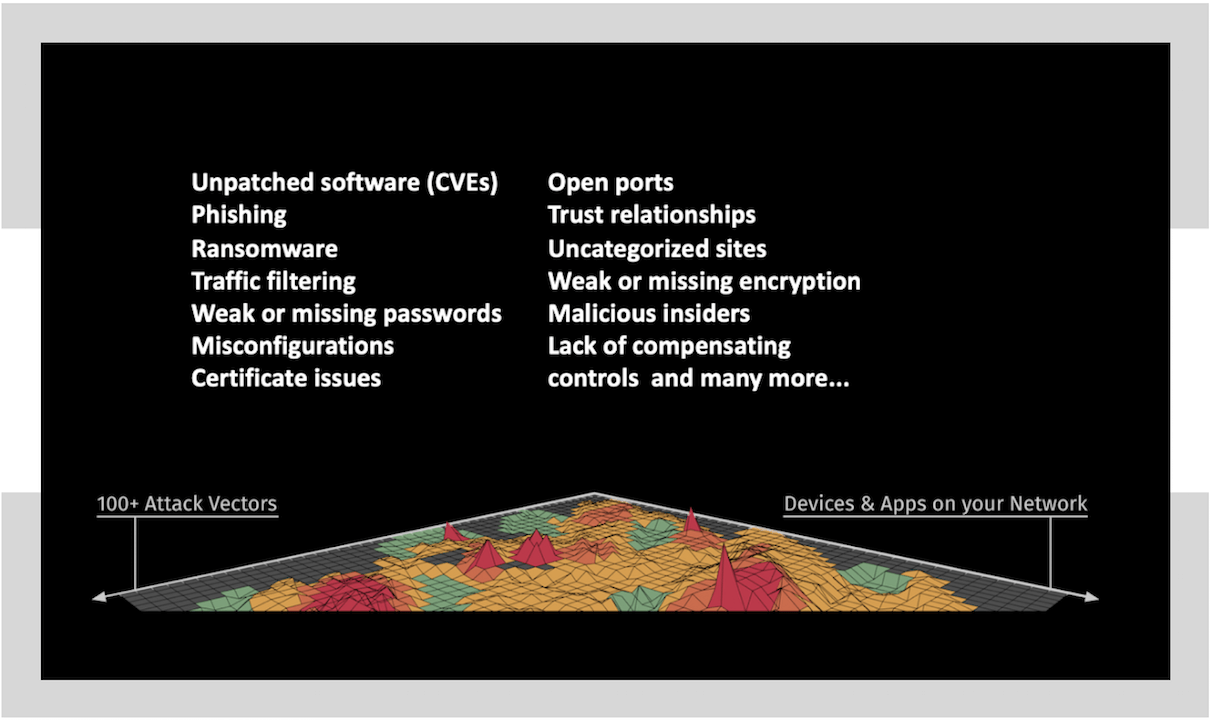
100+ Attack Vectors
100+ Attack Vectors
Balbix performs continuous monitoring and identification of vulnerabilities and other risk items for each asset across 100+ attack vectors, for example:
- Unpatched software (CVEs).
- Phishing.
- Web and ransomware.
- Default, weak or reused passwords.
- Encryption issues – missing encryption or improper encryption.
- Misconfiguration.
- Certificate issues.
1-Hour Deployment
1-Hour Deployment
The deployment of Balbix into your environment is quick and easy.
-
Balbix sensors and appliances are placed to span a suitable subset of north-south and east-west network traffic in your environment.
-
As an optional step, you can deploy lightweight Balbix host sensors or connect Balbix to your enterprise data sources, such as Active Directory, AWS configuration, logs, etc.
-
Within 24 hours, the Balbix dashboard surfaces a 100x more accurate view of cyber-risk than any other method, including asset inventory, historical patching posture, password-related issues, missing encryption, easily phish-able users, and much more.
Cyber-Risk Reporting for Your Board of Directors
How should you quantify cybersecurity posture for your board of directors and C-suite colleagues? Boards and senior executives have three main questions about cybersecurity and breach risk:
- Where is the organization on the cyber-risk spectrum?
- Where should the organization be?
- How can the organization get to where it should be?
Unfortunately, due to the massive size and complexity of the enterprise attack surface and the practically unlimited permutations and combinations by which the adversary can carry out a cyberattack, you know how difficult it is to analyze your overall cybersecurity posture and calculate your organization’s breach risk. Furthermore, because of this vague understanding of security posture, you and your colleagues struggle to agree on where in the spectrum your organization ought to be, i.e., to agree on when cybersecurity is “done” for your organization.
How exactly should you quantify cybersecurity posture for your board of directors and C-suite colleagues? Read this solution brief to learn more.

Resource Library: Insights for CISOs and SecOps Teams
Contact Our Cyber Risk Modeling Experts