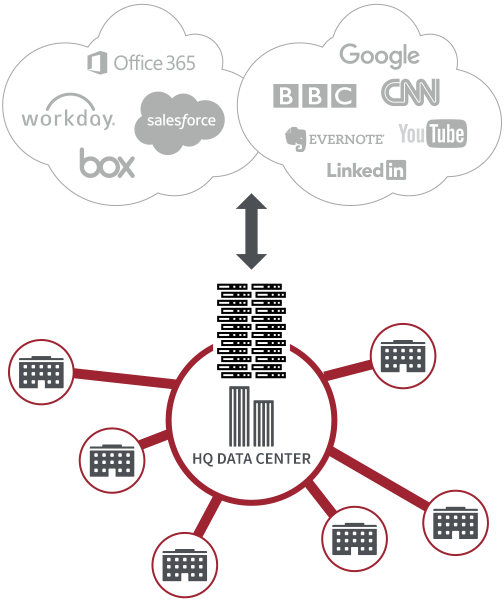
Transform the Way You Deliver Internet Security Services
Magic Quadrant for Secure Web Gateways
Product Showcase for Cyber Security
Web Security
Cherub's services provide you with a secure Internet and web gateway delivered as a service. We will deliver a full security stack with all the in-depth protection you’ll ever need. Just point your office or user traffic to the Cloud-based platform, and it instantly begins stopping malware, advanced threats, phishing, browser exploits, malicious URLs, botnets, and more. Born in the cloud and built for speed, the platform helps you break free from traditional appliance models, cut MPLS and network costs, and restore security in a cloud-first world.
Cloud DLP
Your users might have left the network, but that doesn’t have to mean your sensitive data will leave with them. Our partner's service the Cloud DLP empowers you to illuminate blind spots by providing protection and visibility where you don’t have it today—and with full content and SSL inspection. Cloud DLP enables you to protect sensitive data with advanced controls and granular policy, which can easily be deployed as part of the Cherub security platform, all while remaining in compliance with regulatory mandates.
Cloud Firewall
With our technology partner's Cloud Firewall brings next-gen firewall controls and advanced security to all users in all locations — for all ports and protocols. This service enables fast and secure local internet breakouts and, because it’s 100 percent in the cloud, there’s no hardware to buy, deploy, or manage. Cloud Firewall, you get security and access controls without the cost, complexity, and performance limitations of next-generation firewall appliances. Your protection follows users wherever they go to provide identical protection and access control.
Bandwidth Control
With the majority of your users and applications in the cloud, and most of your traffic now bound for the Internet, it makes sense to move your security and controls to the cloud, too. By implementing our Bandwidth Control — part of the Cloud Security Platform — you can route traffic locally to the Internet, providing great performance and the samelevel of protection for all users, across all locations. Because it is 100% cloud based, you can enforce bandwidth management policies across the organization from a single console, and there is no hardware or software to deploy or manage.
The benefits of enabling secure network transformation
Transform your Security Model
Embrace a direct-to-cloud security stack that protects user and offices, while breaking free from costly appliances and network infrastructure.

More than just Web Security
With multiple security techniques including Sandboxing, Cloud Firewall, Content and URL Filtering, DLP, and CASB, you’ll deliver airtight internet security across all ports and protocols.

Unlimited Capacity
With over 100 data centers, performance from any location is lighting fast, and you’ll never run out of capacity.

Full SSL Visibility
Inspect full SSL across all ports and protocols and never run out of inspection capacity. Try that with an appliance!

Fully Integrated
We built a platform so you don’t have to. Enjoy integrated policies and contextual threat visibility from day one.
Our security cloud processes up to 50 billion transactions per day
Any threat detected is instantly shared and blocked across all our complete cloud.
Customer Stories
Related Solutions
OUR PARTNERS



Contact Our Secure Internet Gateway Experts